
Storage units are packed with valuables from personal mementos to business records and people expect those belongings to stay secure. Now get this. Over 90 percent of modern storage facilities use multilayered security systems combining physical barriers, electronic monitoring, and biometric controls. But the surprise is that even with all this tech, it is the way these security features work together that truly keeps your stuff safe, not just any single device.
| Takeaway | Explanation |
|---|---|
| Physical and electronic security are essential. | A combination of physical barriers and advanced technology is crucial for effective protection of stored items. |
| Understand access control systems. | These systems ensure only authorized individuals can access storage areas, enhancing overall security. |
| Regular security evaluations are necessary. | Continuous assessments help identify vulnerabilities and ensure the effectiveness of security measures over time. |
| Look for multilayered security features. | Facilities with layered security provide multiple defenses against theft and damage, improving your belongings’ safety. |
| Choose facilities with on-site security. | On-site personnel during business hours adds an extra layer of immediate protection and response capability. |
Storage unit security features represent a comprehensive system of protective measures designed to safeguard personal and commercial property during storage. These features go beyond simple padlocks and encompass a sophisticated network of technological and physical security protocols that ensure the integrity and safety of stored items.
Physical security represents the foundational layer of storage unit protection. According to NIST Security Guidelines, robust storage security begins with strategic design elements that deter unauthorized access. Key physical security components include:
Modern storage facilities leverage advanced technological solutions to enhance security. Electronic security features provide multiple layers of protection beyond traditional mechanical barriers. These sophisticated systems include:
Access Control Systems
The most critical technological security feature is the access control system. These digital gatekeepers ensure that only authorized individuals can enter specific storage areas. Typically, these systems incorporate unique identification methods such as:
By implementing comprehensive security features, storage facilities create a multilayered defense mechanism that protects valuable possessions from potential theft, damage, or unauthorized access. The combination of physical infrastructure and technological innovations provides customers with peace of mind and robust protection for their stored items.
Storage unit security is far more than a luxury—it is a critical necessity for protecting valuable personal and professional assets. The importance of robust security measures extends beyond simple protection from theft, encompassing comprehensive safeguarding against multiple potential risks.
Personal and professional belongings represent significant financial and emotional investments. According to NIST Security Guidelines, inadequate security infrastructure can expose individuals to substantial financial losses and potential identity risks. Comprehensive security features prevent unauthorized access, ensuring that your possessions remain protected from potential threats.
Key risks that storage unit security mitigates include:
Beyond physical protection, storage unit security provides critical psychological reassurance. Knowing that your belongings are secure allows individuals to focus on other life priorities without constant worry. When selecting storage solutions, consider facilities that offer comprehensive protection strategies for your possessions.
Modern storage security is a multilayered approach that addresses various potential vulnerabilities. Effective security strategies combine physical barriers, technological monitoring, and rigorous access control protocols. This comprehensive approach ensures that your valuable items are protected through multiple defensive mechanisms.
Factors that contribute to superior storage unit security include:
By understanding and prioritizing storage unit security, individuals and businesses can significantly reduce potential risks, protect valuable assets, and maintain peace of mind during storage periods.
Storage unit security features represent a diverse and sophisticated array of protective technologies designed to safeguard valuable personal and commercial possessions. Understanding these security mechanisms is crucial for individuals seeking comprehensive protection for their stored belongings.
Physical security represents the first line of defense in storage unit protection. According to Newport News Police Department guidelines, effective physical security goes beyond simple padlocks and encompasses multiple protective layers. Advanced physical security features include:
Electronic surveillance technologies provide an additional layer of protection that significantly enhances storage unit security. Modern monitoring systems integrate multiple technological components to create comprehensive security networks. Learn more about preparing and protecting your storage items to complement these advanced security features.
Key electronic monitoring components include:

Access control represents the most sophisticated aspect of storage unit security, utilizing advanced identification and verification technologies. These systems ensure that only authorized individuals can enter specific storage areas. Cutting-edge access control methods encompass:
By implementing these comprehensive security features, storage facilities create multilayered defense mechanisms that protect valuable possessions from potential unauthorized access, theft, and environmental risks.
Below is a table summarizing the main types of storage unit security features and their key characteristics, helping you compare how each category contributes to overall protection.
| Security Feature Category | Example Components | Primary Purpose |
|---|---|---|
| Physical Security Mechanisms | Perimeter fencing, disk locks, reinforced doors, lighting | Prevent unauthorized physical entry |
| Electronic Monitoring Systems | Surveillance cameras, alarms, digital recording, heat sensors | Detect and record suspicious activities |
| Access Control Technologies | Biometric scanners, access cards, PIN codes | Restrict access to authorized users |
| Professional On-Site Security | Security personnel during business hours | Provide real-time human response |
| Redundant Security Protocols | Backup alarms, continuous monitoring | Ensure coverage if another layer fails |
Storage unit security is a complex, interconnected system where multiple protective technologies collaborate seamlessly to create a comprehensive defense mechanism. Understanding how these diverse security features interact is crucial for appreciating the sophisticated protection provided to stored belongings.
According to NIST Security Guidelines, effective security relies on a multilayered approach that integrates different technological and physical components. This strategy ensures that if one security layer fails, subsequent layers provide continued protection.
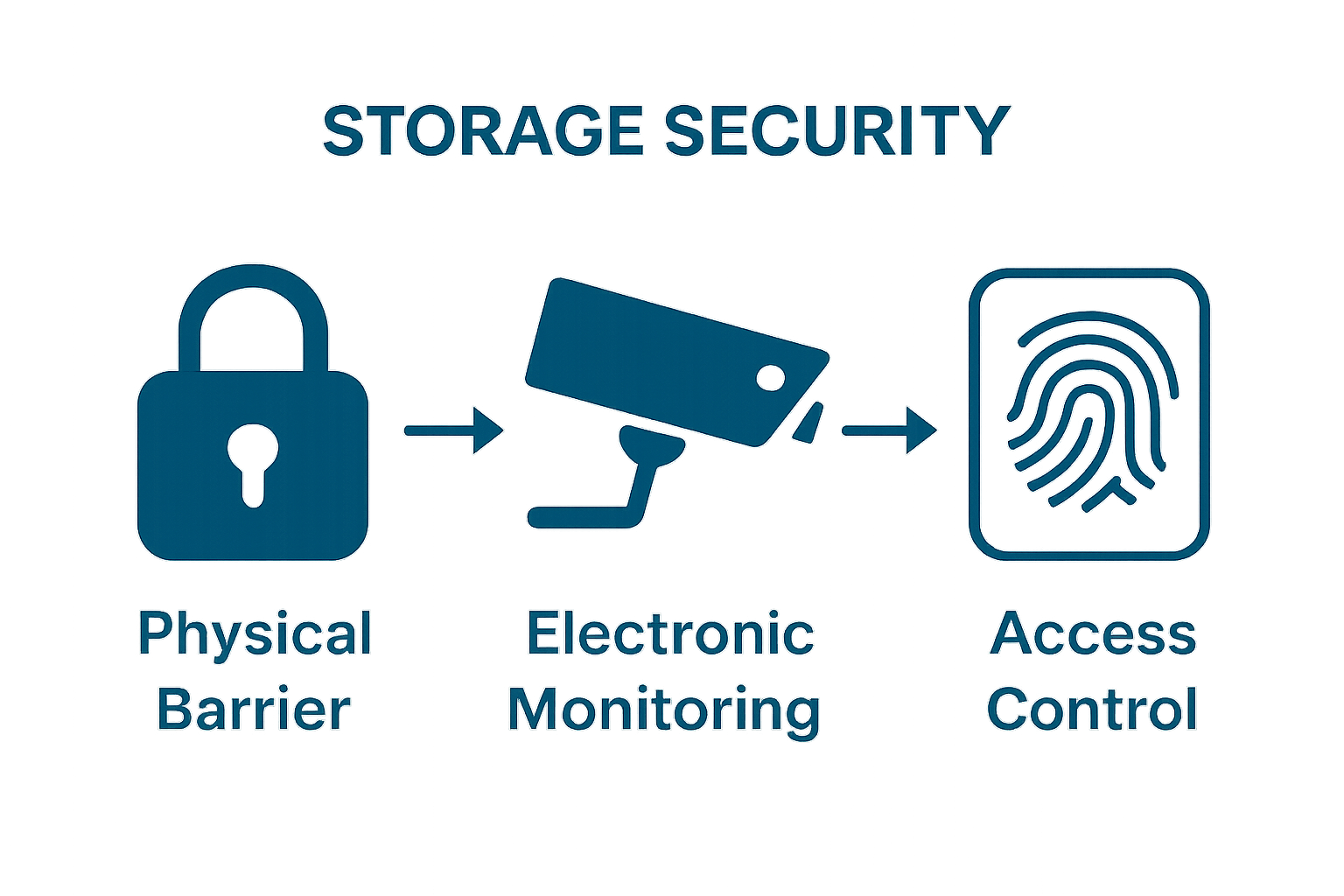
Key layers of integrated security include:
Modern storage unit security features operate through sophisticated digital communication networks. Electronic systems continuously communicate and cross-validate information, creating a dynamic and responsive security environment. Learn more about preparing your items for secure storage to complement these advanced security integrations.
Technological communication pathways involve:
The ultimate goal of integrated storage unit security is creating a holistic protection ecosystem. Each security feature acts like an intelligent component within a larger, interconnected system. This approach transforms individual security mechanisms into a comprehensive, adaptive defense network.
Components of the holistic security ecosystem include:
By understanding how storage unit security features collaborate, customers can appreciate the sophisticated technological infrastructure protecting their valuable possessions. The integration of physical, electronic, and intelligent systems provides an unprecedented level of comprehensive security.
Evaluating storage unit security features requires a comprehensive and systematic approach that goes beyond superficial assessments. A thorough evaluation involves analyzing multiple dimensions of security performance, technological capabilities, and real-world effectiveness.
According to NIST Security Guidelines, effective security assessment demands precise measurement of multiple performance indicators. Quantitative metrics provide objective insights into the functionality and reliability of security systems.
Key performance evaluation metrics include:
Modern security systems require continuous technological vulnerability testing. Comprehensive security evaluations involve simulated scenarios that challenge existing protective mechanisms. Learn more about preparing your items for secure storage to complement your understanding of security assessments.
Critical vulnerability assessment components include:
Evaluating storage unit security extends beyond technological capabilities to include human factors and operational effectiveness. Holistic assessment approaches consider the integrated performance of technological and human security elements.
Comprehensive effectiveness indicators encompass:
By implementing rigorous, multidimensional evaluation strategies, storage facilities can ensure their security features provide robust, reliable protection for customers’ valuable possessions. The combination of quantitative metrics, technological assessments, and holistic performance indicators creates a comprehensive security evaluation framework.
The table below organizes common evaluation criteria and metrics used to assess the effectiveness of storage unit security features, offering a quick comparison of what each assessment method focuses on.
| Evaluation Method | Key Metrics or Indicators | Focus Area |
|---|---|---|
| Quantitative Performance Metrics | Access attempt detection rates, system uptime, surveillance coverage | Objective functionality and reliability |
| Technological Vulnerability Assessment | Penetration testing, breach simulations, protocol analysis | Identifying weak points and risks |
| Holistic Effectiveness Indicators | Staff training, incident history, customer feedback, compliance | Operational performance and user trust |
Worried about leaving your valuable belongings behind in a storage unit? After reading about the multi-layered physical and electronic security features in our article, it is clear how vulnerable your assets can be without proper protection. Many people feel anxious that their documents, keepsakes, or business assets might fall victim to theft, unauthorized access, or unexpected environmental threats. You deserve a storage solution that delivers not just basic locks, but a complete system for peace of mind.
At US Pro Logistics, we put your security concerns first by offering storage solutions that cover advanced features such as continuous video monitoring, secure access controls, and regular security audits. We make it easy to combine your moving needs with secure, modern storage. Whether you are planning a residential or business relocation or need short-term storage while settling in, our family-owned team supports you at every step. Contact us now for a complimentary quote and discover how our trusted experts deliver the secure logistics experience you deserve. Your belongings matter. Protect them today with the professional touch of US Pro Logistics.
Key physical security features include perimeter fencing with controlled entry points, well-lit premises, surveillance cameras, electronic gate access with personalized codes, and on-site security personnel during business hours.
Electronic monitoring systems use high-resolution digital cameras, alarm systems, and remote monitoring technologies to provide continuous surveillance and immediate notifications of any potential security breaches.
An access control system restricts entry to authorized individuals using methods such as personalized access cards, unique PIN codes, and biometric authentication, ensuring that only those permitted can access the stored items.
Evaluating effectiveness involves assessing quantitative performance metrics, conducting technological vulnerability assessments, and reviewing holistic effectiveness indicators such as staff training, historical incident documentation, and compliance with industry standards.
USDOT 3664256 This number is required for any company that operates commercial vehicles in interstate commerce (across state lines). It helps identify and track the safety performance and compliance of transportation companies.
MC 1268070 This number is specifically for companies involved in the transportation of goods or passengers for hire across state lines. It’s necessary for carriers operating in the moving industry and ensures they are authorized to operate as interstate carriers.