Securing your personal and business data is not just about locking it away. Studies show that 60 percent of small companies go out of business within six months of a data breach. Surprising, right? Most people believe encryption alone can keep their information safe but the real safeguard comes from a mix of physical protection, advanced protocols, and constant monitoring. The real question is, how secure is your information when more than one layer is at play?
| Takeaway | Explanation |
|---|---|
| Implement multi-layered security | Combine physical security, encryption, and access control for comprehensive protection. |
| Prioritize encryption technologies | Use advanced encryption methods to protect data at rest and in transit. |
| Adhere to regulatory compliance | Ensure secure storage solutions meet industry-specific standards to avoid legal issues. |
| Utilize monitoring and threat detection | Integrate AI tools to detect anomalies and threats in real-time for enhanced security. |
| Adopt hybrid storage solutions | Combine physical and cloud storage for flexibility and robust data protection. |
Secure storage solutions represent comprehensive systems designed to protect sensitive data, digital assets, and physical materials from unauthorized access, theft, damage, and potential security breaches. These solutions encompass a wide range of technologies, strategies, and practices that safeguard information across physical and digital environments.
Secure storage solutions integrate multiple protective mechanisms to ensure data integrity and confidentiality. At their fundamental level, these systems combine physical security, technological encryption, access controls, and strategic management protocols. According to the National Institute of Standards and Technology (NIST), effective secure storage requires a multi-layered approach that addresses potential vulnerabilities across different storage mediums.
Key components of robust secure storage solutions include:
Implementing secure storage solutions is crucial for protecting sensitive information in an increasingly digital and interconnected world. Organizations and individuals face significant risks from potential data breaches, including financial losses, reputational damage, and legal consequences. Secure storage is not merely a technological choice but a critical strategic imperative that supports operational resilience and maintains stakeholder trust.
Businesses, government agencies, healthcare providers, and educational institutions all rely on secure storage solutions to:
By integrating comprehensive secure storage strategies, organizations can create robust defense mechanisms that adapt to evolving technological landscapes and emerging security challenges.
Below is a comparison table summarizing the main types of secure storage solutions discussed, highlighting their distinguishing features and strengths.
| Storage Type | Description | Key Features/Strengths |
|---|---|---|
| Physical Storage | Tangible protection in controlled environments | Hardware Security Modules, Secure Server Rooms, Biometric Cabinets |
| Digital/Cloud-Based Storage | Cloud-based platforms and remote digital protection | End-to-End Encryption, Automatic Backup, Geographically Distributed |
| Hybrid Storage | Combination of physical and digital/cloud methods | Flexibility, Redundancy, Multiple Layers of Defense |
This table outlines the core components and features found within effective secure storage solutions, supporting clearer understanding of how each element strengthens overall protection.
| Component | Role in Secure Storage | Example Features |
|---|---|---|
| Physical Security | Prevents unauthorized physical access | Controlled entry, Biometric locks, Tamper-resistant devices |
| Digital Encryption | Protects data through cryptographic transformation | End-to-End Encryption, Zero-Knowledge Architecture |
| Access Management | Determines and regulates user access | Multi-Factor Authentication, Automatic Access Revocation |
| Compliance Frameworks | Ensures adherence to legal and industry standards | HIPAA, Financial Regulatory Standards |
| Threat Monitoring | Detects and responds to suspicious activity | AI-Based Anomaly Detection, Real-Time Alerts |
Secure storage solutions represent sophisticated technological frameworks designed to protect critical information through comprehensive security mechanisms. These advanced systems go beyond basic data protection, integrating multiple layers of defense to ensure comprehensive safeguarding of sensitive digital and physical assets.
Encryption serves as the foundational pillar of secure storage solutions. According to the National Cyber Security Centre (NCSC), robust secure storage solutions must implement sophisticated encryption protocols that protect data both during transmission and while at rest. Modern encryption technologies utilize complex algorithms that transform readable data into unreadable code, making unauthorized access exponentially more challenging.
Key encryption features include:
Effective secure storage solutions implement granular access control mechanisms that regulate who can view, modify, or transfer specific information. These systems create intricate permission structures that allow organizations to define precise user roles, limiting potential security vulnerabilities. Access control goes beyond simple password protection, incorporating sophisticated user authentication protocols that continuously validate user identities.
Critical access control elements encompass:
Modern secure storage solutions integrate advanced threat detection technologies that provide real-time monitoring and rapid response capabilities. These systems utilize artificial intelligence and machine learning algorithms to identify potential security anomalies, unauthorized access attempts, and suspicious behavioral patterns. By implementing proactive monitoring mechanisms, organizations can prevent potential breaches before they occur and maintain the integrity of their stored information.
Secure storage solutions have evolved dramatically to address the complex and diverse security requirements of modern organizations and individuals. These solutions range from physical infrastructure to cloud-based platforms, each designed to meet specific data protection and accessibility needs across different technological environments.
Physical storage solutions represent traditional yet critical approaches to securing sensitive information. According to Stanford University’s Secure File Storage research, these solutions focus on tangible protection mechanisms for critical data assets. Physical storage security encompasses secure on-site data centers, hardware-encrypted storage devices, and controlled access environments that prevent unauthorized physical interactions.
Key physical storage solutions include:
Digital storage solutions represent the most dynamic and adaptable secure storage category. These platforms leverage advanced cloud technologies, providing scalable and flexible data protection strategies that transcend traditional physical limitations. Cloud-based solutions offer significant advantages in terms of accessibility, redundancy, and advanced security protocols.
Comprehensive digital storage solutions typically feature:
Hybrid secure storage solutions combine physical and digital storage strategies, creating comprehensive protection frameworks that leverage the strengths of multiple technologies. These sophisticated systems allow organizations to maintain granular control over their data while benefiting from cloud-based flexibility and on-premise security measures. By integrating multiple storage approaches, hybrid solutions provide unprecedented levels of data protection, ensuring that sensitive information remains secure across various technological environments.
Secure storage solutions act as sophisticated guardians, implementing multi-layered protection strategies designed to shield sensitive information from potential threats. These comprehensive systems go beyond simple data storage, creating intricate defense mechanisms that proactively safeguard digital and physical assets against unauthorized access, data breaches, and potential system vulnerabilities.
Data encryption represents the primary mechanism through which secure storage solutions protect assets. According to the National Institute of Standards and Technology (NIST), effective protection requires transforming readable data into complex, unreadable code that can only be deciphered with specific authentication credentials. This process ensures that even if unauthorized individuals gain physical access to storage media, the information remains completely incomprehensible.
Key encryption protection strategies include:
Secure storage solutions employ sophisticated threat mitigation techniques that continuously monitor and respond to potential security risks. These systems utilize advanced artificial intelligence and machine learning algorithms to detect unusual access patterns, unauthorized modification attempts, and potential cyber intrusions. The goal is not just protection but proactive threat prevention.
Critical threat mitigation features encompass:
Beyond immediate protection, secure storage solutions integrate robust redundancy frameworks that ensure data survival and accessibility under various challenging scenarios. These systems create multiple backup copies across geographically distributed locations, implementing the critical 3-2-1 backup rule that guarantees data can be recovered even if primary storage systems experience catastrophic failures. By distributing risk and creating multiple recovery pathways, these solutions provide organizations and individuals with unprecedented data protection and business continuity capabilities.
Secure storage solutions have become essential across numerous industries, transforming how organizations protect, manage, and leverage their most critical information assets. These sophisticated systems provide targeted protection strategies that address unique security challenges in diverse professional environments, ensuring data integrity and confidentiality.
Medical data represents one of the most sensitive information categories, requiring exceptional security measures. According to the National Institute of Standards and Technology (NIST), healthcare institutions must implement comprehensive secure storage solutions that comply with strict regulatory requirements like HIPAA. These systems protect patient records, diagnostic information, and medical research data from unauthorized access while maintaining seamless accessibility for authorized medical professionals.
Key healthcare secure storage applications include:
Financial institutions rely extensively on secure storage solutions to protect highly sensitive transactional and personal financial information. These systems serve as critical defense mechanisms against potential cyber threats, fraud, and unauthorized financial access. Advanced secure storage technologies enable banks and financial service providers to maintain robust protection while facilitating efficient digital transactions and record-keeping.
Critical financial secure storage features encompass:
Government agencies and military organizations utilize the most advanced secure storage solutions to safeguard classified information, national security intelligence, and sensitive diplomatic communications. These systems incorporate multiple layers of encryption, restricted access protocols, and sophisticated monitoring mechanisms that prevent potential security breaches and unauthorized information disclosure. By implementing comprehensive secure storage strategies, these organizations can maintain the confidentiality and integrity of critical national security assets.
Worried about protecting your valuable possessions during a move or long-term storage? As the article explains, secure storage is more important than ever, with risks like unauthorized access, data breaches, and loss of sensitive materials impacting individuals and organizations alike. Whether you are a homeowner, business owner, or government agency, finding a trusted partner for truly secure storage is often challenging. You might be seeking a solution that includes advanced physical protections, continuous monitoring, and strict access controls, just as described in the article’s comprehensive overview of modern secure storage solutions.
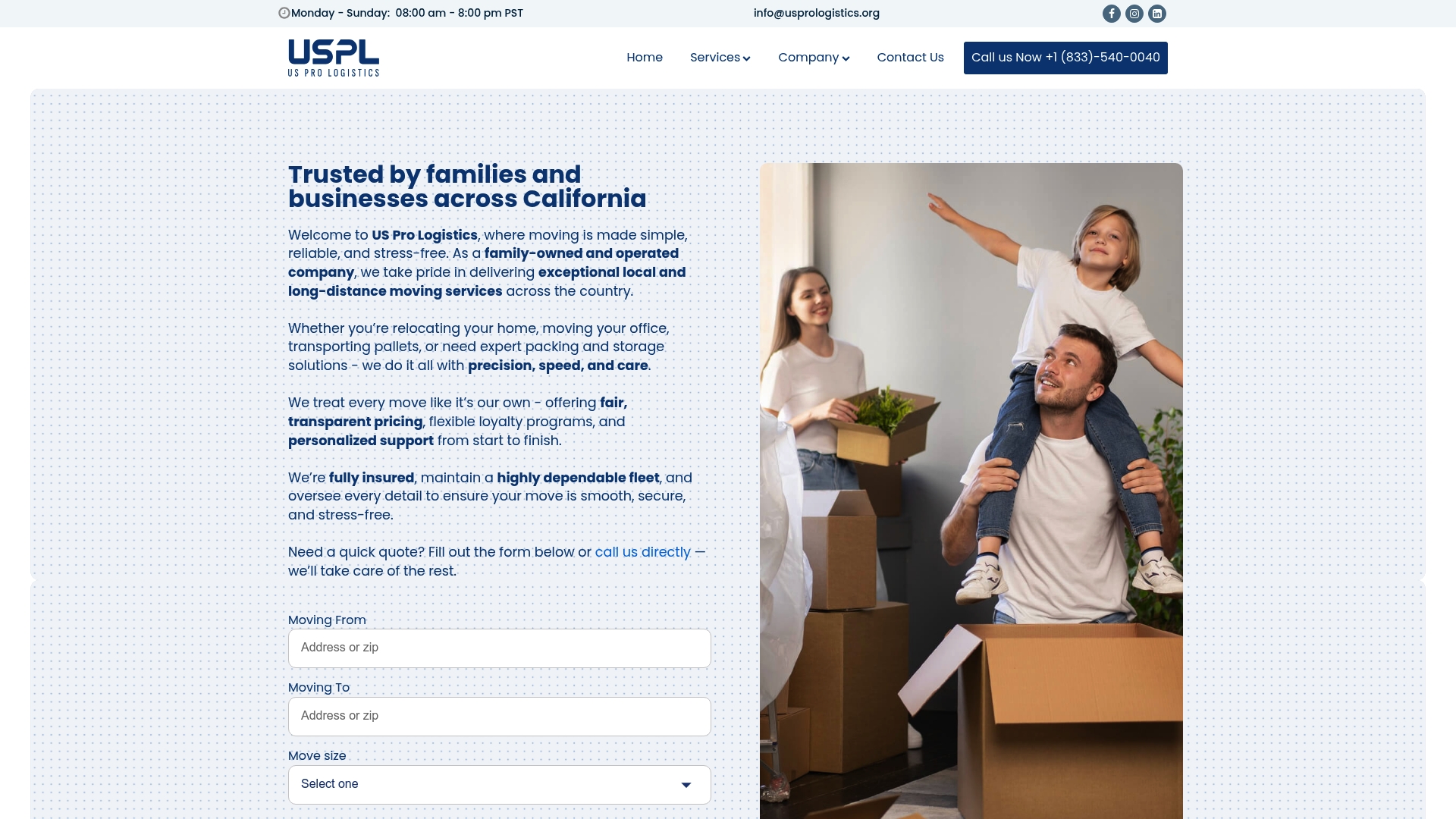
US Pro Logistics delivers exactly what you need with professionally managed, secure storage and logistics services. Our team helps you safeguard your belongings using best-in-class technology and physical security, all while guaranteeing strict oversight and accountability. Get the peace of mind you deserve, and request a quote or learn more about our commitment to safety at US Pro Logistics. If you want specific details about secure storage or other moving services, explore our Uncategorized section. Don’t wait—contact us today and experience stress-free storage solutions trusted throughout California and across the US.
Secure storage solutions are comprehensive systems designed to protect sensitive data and physical materials from unauthorized access, theft, and security breaches. They include technologies, strategies, and practices that ensure the security and integrity of information.
Implementing secure storage is crucial as it protects sensitive information against data breaches, financial losses, and reputational damage while ensuring compliance with regulations and maintaining stakeholder trust.
The core components include physical security measures, digital encryption techniques, access management protocols, and frameworks for compliance with regulatory standards.
Encryption technologies transform readable data into unreadable code, making unauthorized access challenging. They often include sophisticated methods like end-to-end encryption and multi-factor authentication to protect data at rest and during transmission.
USDOT 3664256 This number is required for any company that operates commercial vehicles in interstate commerce (across state lines). It helps identify and track the safety performance and compliance of transportation companies.
MC 1268070 This number is specifically for companies involved in the transportation of goods or passengers for hire across state lines. It’s necessary for carriers operating in the moving industry and ensures they are authorized to operate as interstate carriers.